There are two major types of SPF failures; SPF hardfail (represented by -all) and SPF softfail (represented by ~all). SPF ~all failure indicates that a sender’s address isn’t explicitly permitted to send emails from your domain. In this case, recipients’ servers mark emails coming from your domain but failing SPF authentication checks as spam.
On the other hand, the SPF -all mechanism indicates that an email resulting in a hardfail status was sent by a sender who is explicitly not permitted to send messages on your behalf. So, all such email messages are outrightly rejected from entering recipients’ mailboxes.
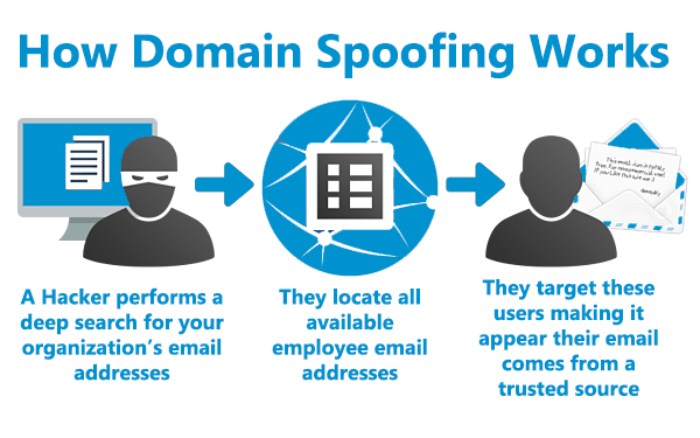
Image sourced from ocd-tech.com
So, Why Should You Use the SPF ~all Mechanism?
It’s true that SPF ~all mechanism makes your email-sending domain a little vulnerable to cyberattacks, but a hardfail restricts many of your legitimate emails from showing up in recipients’ mailboxes at all (not even in the spam folder). This is because of SPF’s incompetence in making a 100% correct distinguishment between genuine and fraudulent messages. As technology is evolving, it’s getting better, but there’s still a long way to go.
So, if you use the SPF ~all mechanism, then both fraudulent emails and genuine emails misconstrued as fraudulent will be marked as spam. In this case, important conversations and marketing emails will still make their way to recipients’ mailboxes. It’s best to combine SPF with DKIM and DMARC to outweigh its shortcoming.

Please remember to set up your SPF record to -all (hardfail) for all non-email-sending domains. Hackers are very keen on exploiting such domains for phishing and spoofing.
